Featured
Table of Contents
What Does A Vpn App Do & How Does It Work?
Consider your internet connection as a tunnel. This tunnel is covered in a layer of file encryption that keeps others from seeing what you're doing online. If you're visiting to your Twitter account, for example, you're passing your account info from your computer to Twitter through a tunnel that no one else has access to.
If you link to a VPN, there's a fast test you can do to see if it's working. and ipleak. net deal totally free tools for validating your IP address, DNS requests and Web, RTC info (basically, everything a VPN covers up). Link to your VPN, run the tests on one or both websites and verify that the information is different.
Now that you understand what a VPN is, it's time to pick one. The very best VPN services fire on all cylinders, providing security, privacy, ease of usage and a large selection of servers. Here are a few things you need to search for when selecting a VPN: VPNs provide an encrypted channel for your information, but that doesn't indicate the VPN itself can't log your personal information.
Spoiler: not all of them do. Unless you're under ISP throttling, a VPN will slow down your web connection. However, some VPN services slow down your speed more than others. Once again, specific item reviews here are essential. Above all, though, it is very important to pick a VPN service with a good reputation.
Explain How A Virtual Private Network (Vpn) Works
VPNs are legal in the majority of nations. Not technically illegal, some nations are more rigorous when it comes to VPN users, so it's finest to consult the laws in your region.
3 each month for each user. Finest UK VPN Solutions We've assembled a list of what we believe are the best VPNs for 2023.
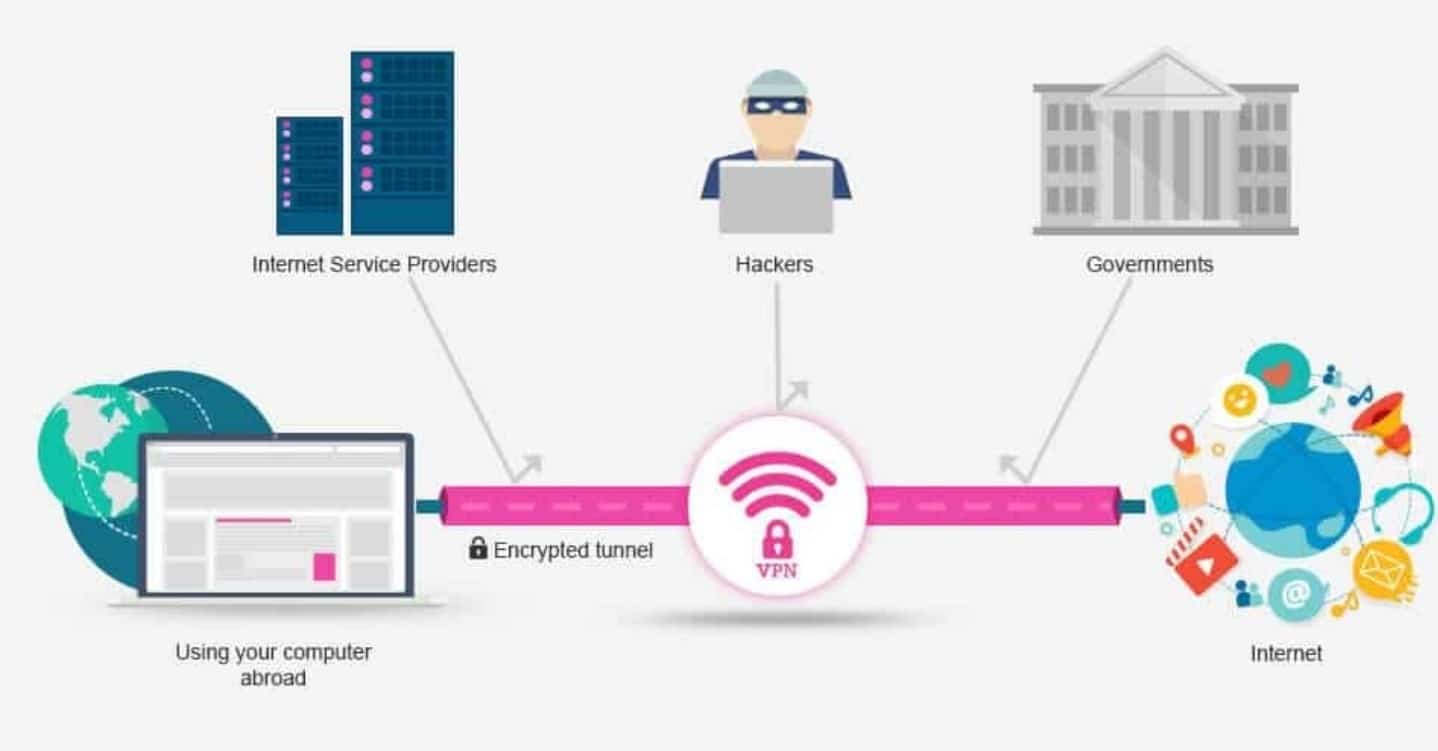
This indicates your Internet Service Provider (ISP) and other 3rd parties can not see which sites you go to or what information you send out and receive online. A VPN works like a filter that turns all your data into "gibberish". Even if somebody were to get their hands on your information, it would be ineffective.
Unencrypted data can be viewed by anyone who has network gain access to and wishes to see it. With a VPN, hackers and cyber crooks can't analyze this information. To check out the information, you need an encryption key. Without one, it would take millions of years for a computer system to analyze the code in case of a brute force attack.
Virtual Private Network (Vpn) Apps On Mobile Devices
: VPN servers basically function as your proxies on the internet. Because the group location information originates from a server in another nation, your actual location can not be figured out. In addition, a lot of VPN services do not keep logs of your activities. Some providers, on the other hand, record your habits, but do not pass this information on to 3rd parties.
Providers and sites often contain content that can just be accessed from certain parts of the world. Requirement connections utilize local servers in the country to identify your area.
A VPN needs to also avoid you from leaving traces, for example, in the type of your internet history, search history and cookies. The file encryption of cookies is specifically important because it avoids 3rd parties from accessing to secret information such as personal information, financial information and other content on sites.
At the web level, regional networks and gadgets might be connected to the universal network and this is where the threat of direct exposure ended up being clear. In 1993, a group from Columbia University and AT&T Bell Labs lastly prospered in developing a kind of very first version of the contemporary VPN, understood as sw, IPe: Software IP file encryption procedure.
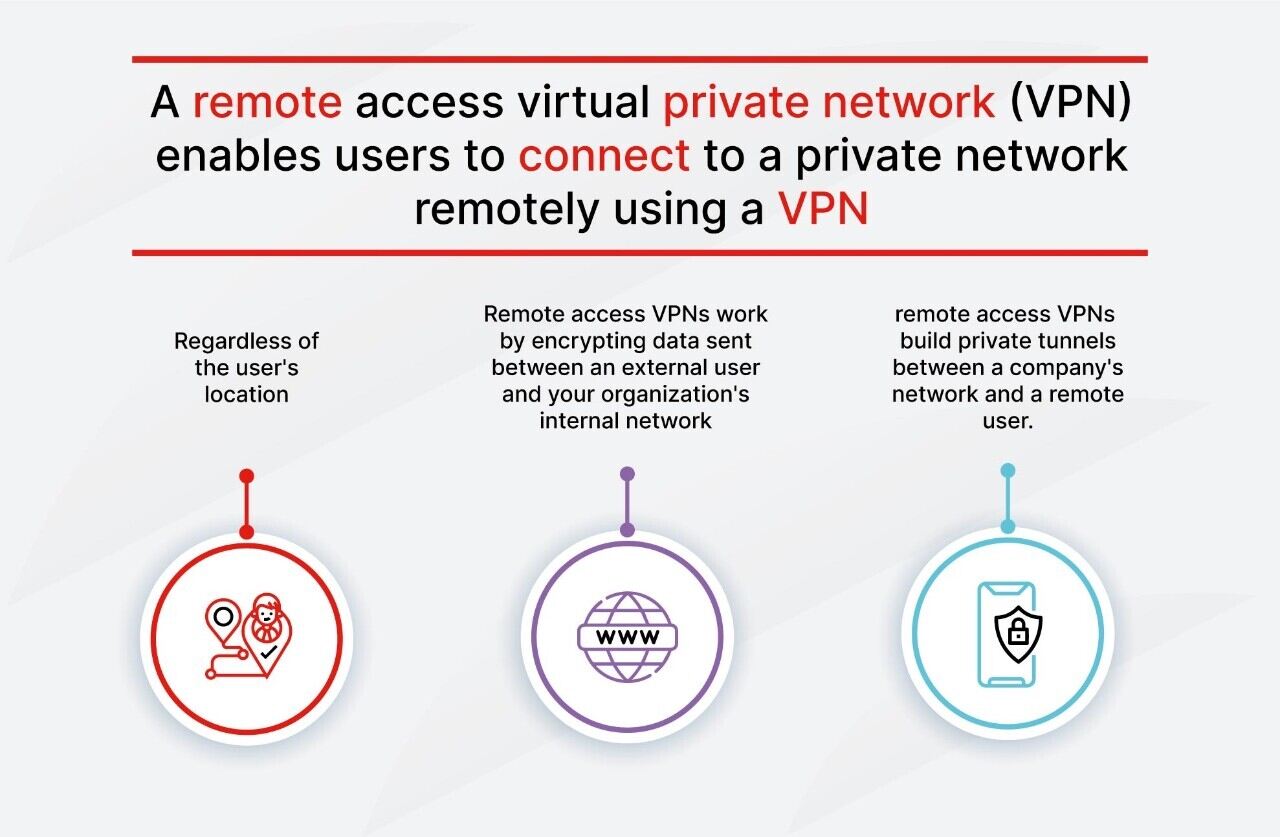
What Is A Vpn In The Remote Workplace
In the U.S.A., Great Britain and Germany, the percentage of VPN users is, however is growing. One of the greatest drivers for VPN adoption over the last few years has actually been the increasing demand for content with geographical access restrictions. For instance, video streaming services such as Netflix or You, Tube make particular videos readily available only in certain countries.
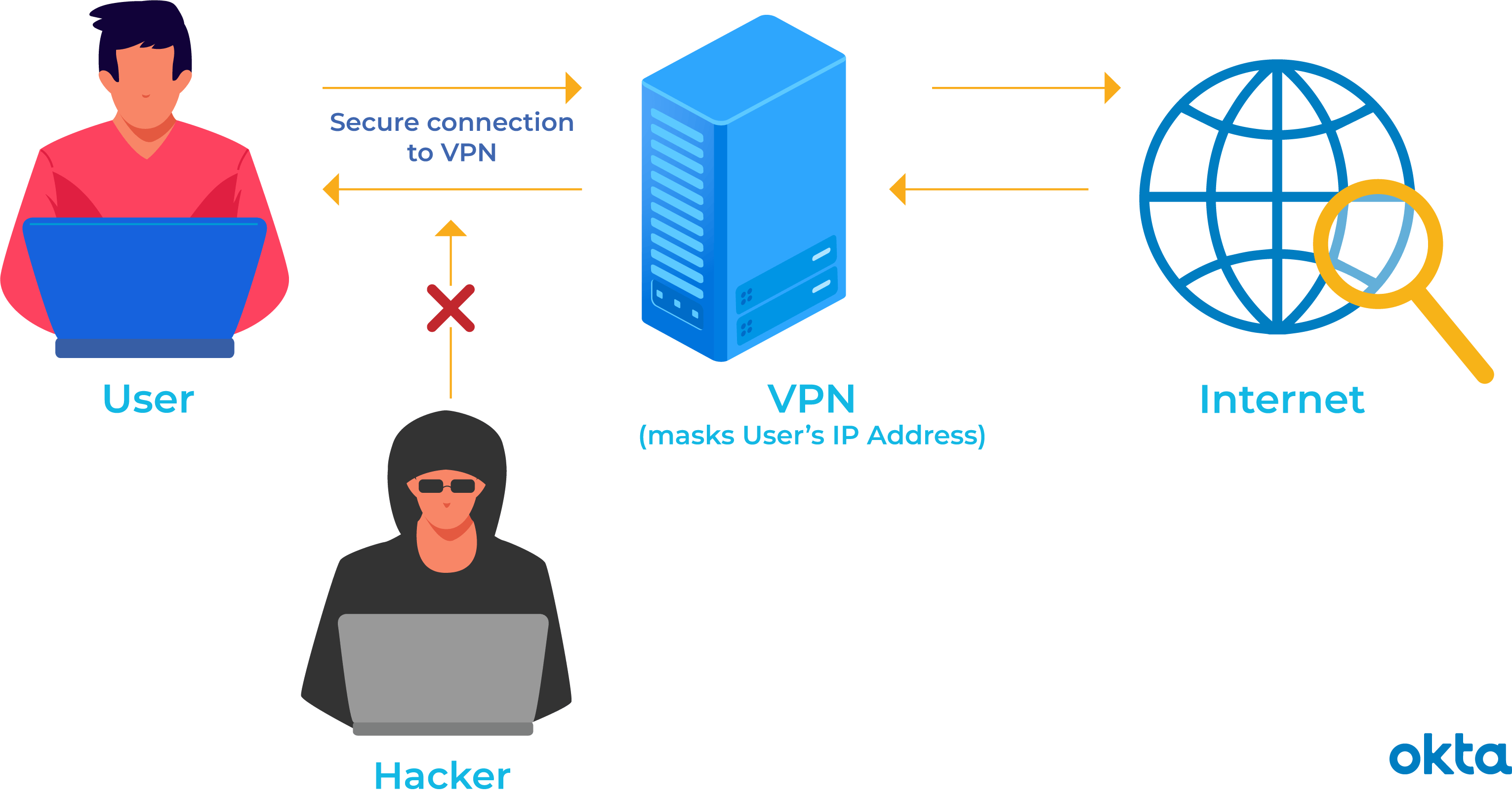
A VPN secures your surfing behavior, which can only be decoded with the aid of a key. Only your computer and the VPN understand this key, so your ISP can not acknowledge where you are surfing. Different VPNs use various encryption processes, however typically function in 3 actions: As soon as you are online, start your VPN.
Your ISP and other 3rd parties can not discover this tunnel. Your gadget is now on the local network of the VPN, and your IP address can be changed to an IP address provided by the VPN server. You can now browse the web at will, as the VPN protects all your personal information.
Site-to-site VPNs are primarily utilized in large companies. They are complex to implement and do not provide the exact same versatility as SSL VPNs. Nevertheless, they are the most efficient way to guarantee communication within and in between large departments. Connecting via a can be thought of as if you were linking your house PC to the company with an extension cable.
Virtual Private Networks (Vpns) - Ncsc.gov.uk
It prevents third parties from accessing and compromising the network connection and secures data all the method to the service provider. It also avoids ISPs from accessing data that, for whatever reason, remains unencrypted and bypasses any limitations on the user's web access (for example, if the government of that country limits web access).
Offered a proper telephone system is readily available, the worker can, for example, connect to the system with a headset and act as if he/she were at their business workplace. Consumers of the business can not even tell whether the worker is at work in the company or in their home office.
Latest Posts
Best Vpn Services For 2023 - Is Yours There?
10 Best Business Vpn Services [2023]: A Comprehensive ...
What Is A Vpn And How Does It Work?